Most people think the web is just pretty pictures and text. Nope.
Here’s the breakdown:
- HTML = structure (bones)
- CSS = design (clothes)
- JavaScript = behavior (the brain — and sometimes, the scammer)
If you click a button, drag something, see a countdown, or get a pop-up — JavaScript is pulling the strings.
Powered by JavaScript
Let’s say I’m a bad actor (but like, a smart one). I don’t need to hack your wallet. I just need to convince you to give me permission — and I’ll do it with a single script dropped inside a legit-looking ad.
Here’s the play-by-play:
1. Load JavaScript Through Ads
- I inject a malicious script into a site like CoinMarketCap or CoinTelegraph.
- The site doesn’t know. The ad network doesn’t notice.
- But your browser? It treats that script like it’s part of the main site — full access.
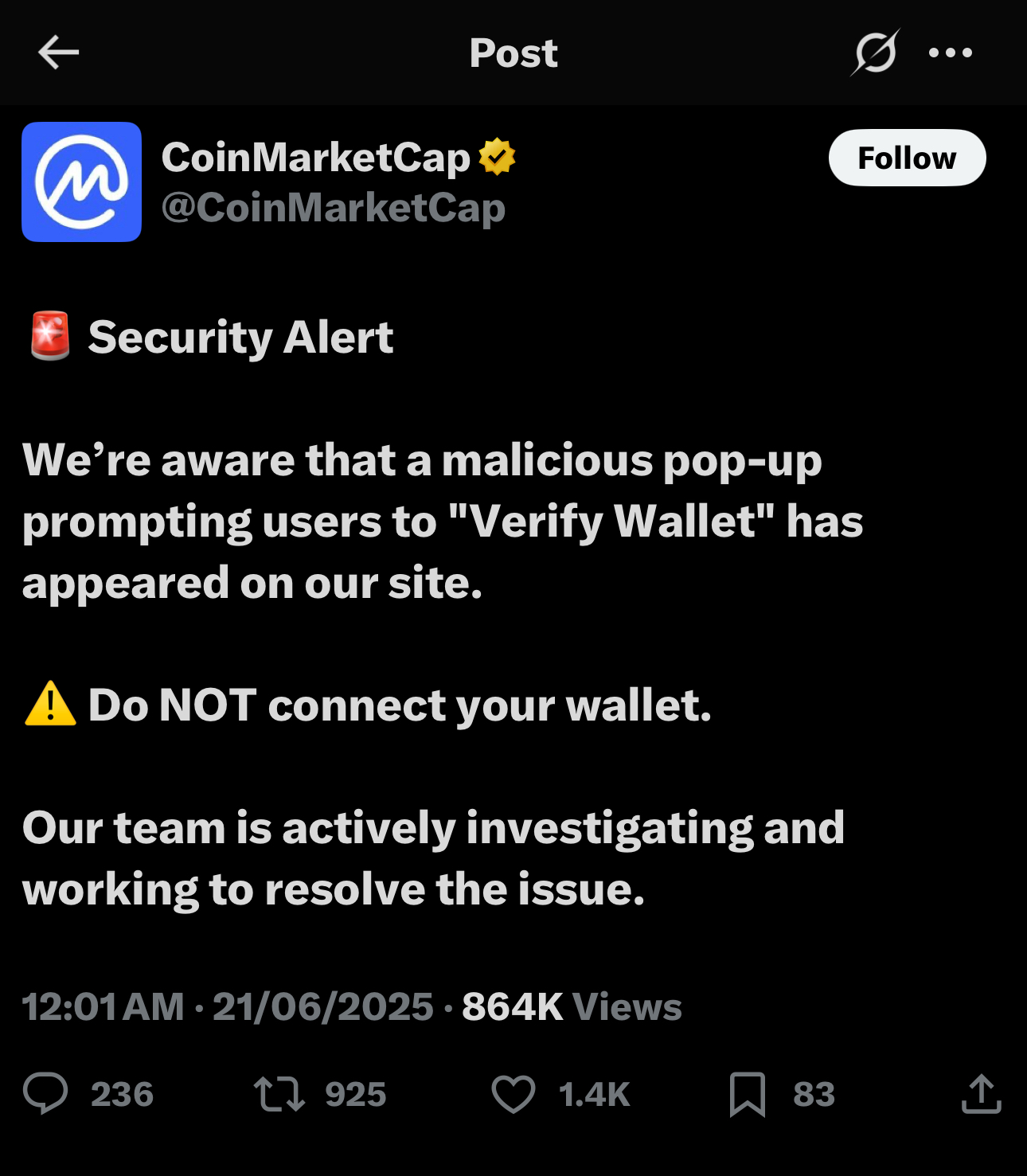
Boom. I’ve now hijacked trust.
2. Render a Fake Airdrop Popup
JavaScript dynamically creates a slick modal:
- Shows your “allocation” (50,000 CTG tokens, worth $5K — how generous 😇)
- Starts a countdown timer (because FOMO)
- Prompts “Connect Wallet” to claim
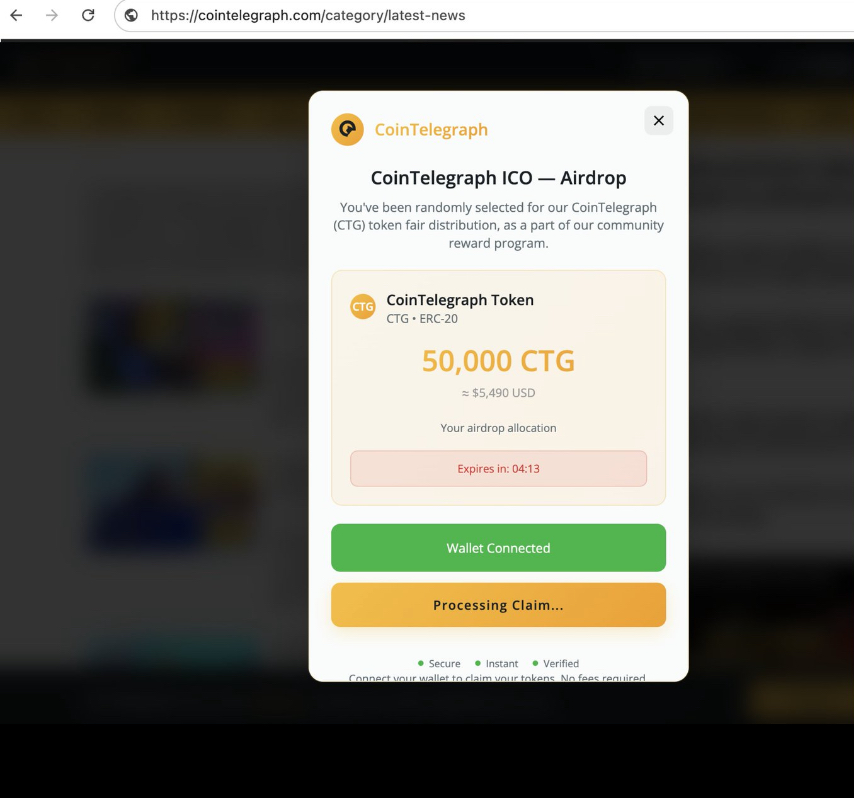
It looks clean because I styled it with CSS. It acts legit because it’s running on a trusted site. But it’s all fake.
3. Use JavaScript to Trigger WalletConnect
Once you click, the script:
- Calls your wallet provider (MetaMask, WalletConnect, etc.)
- Asks for a signature — sometimes a blank one, sometimes approval for a spending contract
You think you’re just verifying. But in the background, I’m using that signature to:
- Transfer your tokens
- Approve malicious contracts
- Drain NFTs
No password needed. Just one signed message. All via JavaScript.
Why JavaScript Is the Perfect Weapon
JavaScript runs:
- Automatically
- In the background
- With the full trust of the site it’s loaded from
It doesn’t ask your permission. It doesn’t need to install anything. And unless your browser isolates it properly (hint: most don’t), it can:
- Track your keystrokes
- Watch your mouse
- Inject HTML
- Hijack wallet requests
- Even fingerprint your device
In other words… JavaScript is friendly until it’s not.
Alright, enough dark side. Here’s how I keep my wallet clean:
- Use uBlock Origin — block those sneaky scripts at the source
- Don’t trust wallet popups unless you triggered them yourself
- Revoke approvals often (like brushing your teeth, but for your crypto)
- Use browser isolation or Brave — reduce JS exposure
- Know what you’re signing — always read that signature request
I love JavaScript. I build with it daily. But I also respect how dangerous it can be when abused.
What happened on CoinTelegraph and CoinMarketCap wasn’t a hack — it was just clever use of JS and user trust.
You don’t need to break in if people open the door for you.
So let’s lock that door.
Crypto is freedom but only if you protect it like it’s already under attack.